Hello Everyone,
I apologise in advance for the length of this post, especially as this is my first technical post [so please be gentle!]. if I can I'd like to ask for some help and/or advice with respect to building a Form that can be used to render a dynamically-changing menu for a user. This needs to be a little bit more sophisticated [but similar in principle] to the "Switchboard" variant that was offered with Access in older releases [i.e. 2007]. [ I am using 2013].
I enclose below some context on the outcome I'm hoping to achieve...
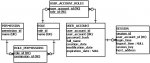
My Access App can authenticate users [simple auto-launch form] at opening. Using a very simple set of related tables [ A user may map to one or more Roles, each of which can map to one or More ACL objects. An ACL object, in this context, then maps to a "Menu Option", which manifests as a record in a Menu Table]. Through this model I can define different roles within my Application that I want to have differing levels of access to functionality through my Menu system.
I had envisioned a simple form with [for example] up to 20 dynamic "button" objects. Each button could be re-labelled [with Menu Description Information, from the Menu Table]. As a result, the "rendering" of a menu would take in 2 key items - one would be the Menu Node [i.e. where are we in the menu structure?] and the other would be the Role ID [i.e. which options from the available list is this User/Role able to "see" on this menu? A Proc could then iterate through some form of Array object [of buttons] and update their attributes with elements from a result set from the Menu table... which itself could be implicitly filtered by means of a join with the ACL and Role tables...
So to the problem...
I am looking for guidance and advice on an approach that would allow me to:-
1. re-enter the form as often as needed, carrying over a global-variable identifier to help the program identify which node of the menu it is supposed to be displaying
2. grab the relevant menu options from the Menu table [dead easy - select "* WHERE menuParent = " {the correct node ID}...
3. filter the result set based on the Role of the Authenticated User [basically a table join; again I am expecting this to be very straightforward]
4. rendering a series of buttons on a Form, with each button dynamically populated with a Menu Item Description that will change as the user navigates through the application... For what it's worth, I figure that handling user choice in this scenario is pretty easy: even though I may change the label of a button, I can set each button to perform the same action [i.e. call a subroutine that assigns a specific value to a working variable] and then jump into some dispatcher logic which figures out what to do based on which button was pushed...
The tricks are:-
1. I'd like to label the buttons dynamically, using content from the "Menu" table
2. I'd like to selectively render buttons, using most likely a join between my "Menu" table and an "ACL" Table that is itself joined to a "Role" table...
3. It is likely self-evident, but I will need a "back" capability, which should be easy as this will typically be a jump "up" the hierarchy to the parent node, but it might be nice to lay out a "breadcrumb trail" along the top of the Menu form, if such a thing is possible?
4. I am entirely happy if the rendering involves using "Visible=false" to "hide" one or more inactive/impermissible menu options, thus leaving "gaps" in the menu structure... [ In fact this might be nice...]
I'll stop with the explanation here, as I've already written far too much [thanks for reading this far]. I'm not wedded to any particular solution, but as I am very much a novice, will strive for simplicity if it is at all possible...
Thanks in advance for any responses!
I apologise in advance for the length of this post, especially as this is my first technical post [so please be gentle!]. if I can I'd like to ask for some help and/or advice with respect to building a Form that can be used to render a dynamically-changing menu for a user. This needs to be a little bit more sophisticated [but similar in principle] to the "Switchboard" variant that was offered with Access in older releases [i.e. 2007]. [ I am using 2013].
I enclose below some context on the outcome I'm hoping to achieve...
My Access App can authenticate users [simple auto-launch form] at opening. Using a very simple set of related tables [ A user may map to one or more Roles, each of which can map to one or More ACL objects. An ACL object, in this context, then maps to a "Menu Option", which manifests as a record in a Menu Table]. Through this model I can define different roles within my Application that I want to have differing levels of access to functionality through my Menu system.
I had envisioned a simple form with [for example] up to 20 dynamic "button" objects. Each button could be re-labelled [with Menu Description Information, from the Menu Table]. As a result, the "rendering" of a menu would take in 2 key items - one would be the Menu Node [i.e. where are we in the menu structure?] and the other would be the Role ID [i.e. which options from the available list is this User/Role able to "see" on this menu? A Proc could then iterate through some form of Array object [of buttons] and update their attributes with elements from a result set from the Menu table... which itself could be implicitly filtered by means of a join with the ACL and Role tables...
So to the problem...
I am looking for guidance and advice on an approach that would allow me to:-
1. re-enter the form as often as needed, carrying over a global-variable identifier to help the program identify which node of the menu it is supposed to be displaying
2. grab the relevant menu options from the Menu table [dead easy - select "* WHERE menuParent = " {the correct node ID}...
3. filter the result set based on the Role of the Authenticated User [basically a table join; again I am expecting this to be very straightforward]
4. rendering a series of buttons on a Form, with each button dynamically populated with a Menu Item Description that will change as the user navigates through the application... For what it's worth, I figure that handling user choice in this scenario is pretty easy: even though I may change the label of a button, I can set each button to perform the same action [i.e. call a subroutine that assigns a specific value to a working variable] and then jump into some dispatcher logic which figures out what to do based on which button was pushed...
The tricks are:-
1. I'd like to label the buttons dynamically, using content from the "Menu" table
2. I'd like to selectively render buttons, using most likely a join between my "Menu" table and an "ACL" Table that is itself joined to a "Role" table...
3. It is likely self-evident, but I will need a "back" capability, which should be easy as this will typically be a jump "up" the hierarchy to the parent node, but it might be nice to lay out a "breadcrumb trail" along the top of the Menu form, if such a thing is possible?
4. I am entirely happy if the rendering involves using "Visible=false" to "hide" one or more inactive/impermissible menu options, thus leaving "gaps" in the menu structure... [ In fact this might be nice...]
I'll stop with the explanation here, as I've already written far too much [thanks for reading this far]. I'm not wedded to any particular solution, but as I am very much a novice, will strive for simplicity if it is at all possible...
Thanks in advance for any responses!